At GoTo, we love our healthcare customers. We have teams and integrations dedicated to giving them the best possible tools and experience. Because of this, we understand how important HIPAA is to our healthcare clients and their business associates.
Last year, I personally became certified in both HIPAA Security and HIPAA Awareness to learn more. In this post, I will give a brief overview of what HIPAA is, cover three of the five major HIPAA rules, and discuss how GoTo handles HIPAA.
What is HIPAA?
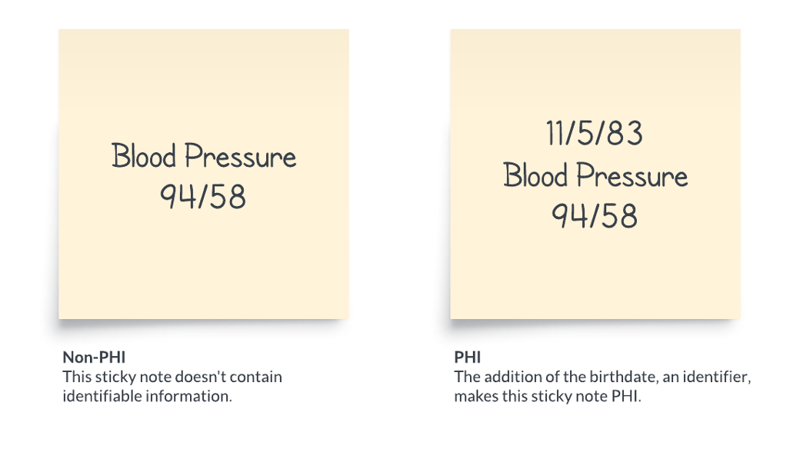
HIPAA stands for the Health Insurance Portability and Accountability Act of 1996. This included Administrative Simplification provisions that required Health and Human Services to adopt national standards. Congress also incorporated into HIPAA provisions that mandated the adoption of federal privacy protections for individually identifiable health information. Individually identifiable health information is more commonly referred to as PHI, or Protected Health Information. There are quite a few identifiers that can qualify as PHI. Some examples include name, address, account numbers, and IP address. The two sticky notes below provide an example of when information is PHI and when it isn’t.
HIPAA applies to covered entities and business associates. Covered entities are the main parties responsible for complying with the HIPAA Rules’ requirements. Covered entities could be medical practices, health plans, healthcare providers, etc. Business associates perform functions or activities on behalf of a covered entity. Business associates could be lawyers, accountants, cloud storage services, etc. The HIPAA Rules generally require a covered entity and business associates to enter into a contract ensuring that the business associate will appropriately safeguard PHI. A contract like this is called a BAA, or Business Associate Agreement.
HIPAA Rules
There are five rules that make up HIPAA:
I am going to talk about three of those rules:
The Privacy Rule establishes national standards for covered entities to protect identifiable health information. This requires that appropriate safeguards be used to protect this information and access to this information is limited to only those who need it. This rule also ensures that individuals have rights to their protected health information to examine, view, and make corrections. The Security Rule is important when you are looking at adding technologies and software.
The Security Rule coincided with the beginning of the evolution from paper processes to electronic processes. Accordingly, PHI stored electronically is called e-PHI. Technologies like electronic health records, computerized physician order entry, and electronic medical imaging were developed to replace traditional paper records. While these technologies create more mobile and efficient workforces, they can also increase potential security risks.
According to the Department of Health and Human Services, “A major goal of the Security Rule is to protect the privacy of individuals' health information while allowing covered entities to adopt new technologies to improve the quality and efficiency of patient care. Given that the health care marketplace is diverse, the Security Rule is designed to be flexible and scalable so a covered entity can implement policies, procedures, and technologies that are appropriate for the entity's particular size, organizational structure, and risks to consumers' e-PHI.”
The final rule I will highlight is the Breach Notification Rule. This rule requires covered entities to provide notification to affected individuals, the Secretary, and, depending on the circumstances, the media, following a breach of unsecured PHI. If the breach occurs with a business associate, they must notify the covered entity.
HIPAA and GoTo
When choosing a service provider who will be a business associate, make sure they can provide you with third-party security reviews and a business associate agreement. Covered entities should choose to work with vendors that will help them maintain their security, privacy, and breach notification policies. When choosing vendors that qualify as business associates, they should also ensure that a business associate agreement is in place, even if the business associate has a third-party HIPAA certification or they are self-certified. A certification does not mitigate the need for a BAA.
When asked about third-party certifications, the Department of Health and Human Services stated, “HHS does not endorse or otherwise recognize private organizations’ “certifications” regarding the Security Rule, and such certifications do not absolve covered entities of their legal obligations under the Security Rule. Moreover, performance of a ‘certification’ by an external organization does not preclude HHS from subsequently finding a security violation.” Therefore, HIPAA compliance is best thought of as an ongoing process rather than a one-time checkbox and will vary depending on the covered entity.
Unlike traditional business associates, GoTo’s services such as GoTo Connect do not require routine access to any PHI. However, GoTo is committed to supporting our clients that are considered covered entities or business associates, and our services can absolutely be used in compliance with HIPAA-based policies and procedures put in place by a covered entity’s compliance officer. Information on how GoTo aligns with the requirements of HIPAA – including the Security Rule and the Breach Notification Rule – can be found in our Business Associate Agreement (BAA), publicly viewable here https://www.goto.com/company/legal/business-associate-addendum. This BAA is incorporated into our standard Terms of Service contract meaning when you sign up to any of our GoTo services a BAA is included and binding on us.
If you are interested in reading about GoTo’s privacy programs and security programs, visit our Trust Center.

